This requires a fairly specific configuration to occur but I didn’t see this documented anywhere so I figured I’d write about it.
If you run your own Enterprise Certificate Authority using the Active Directory Certificate Authority and have used the default ‘Domain Controller’ template you may run into this problem.
By default, it does not appear the ‘Domain Controller’ Certificate Template has the ‘Autoenroll’ permission available:
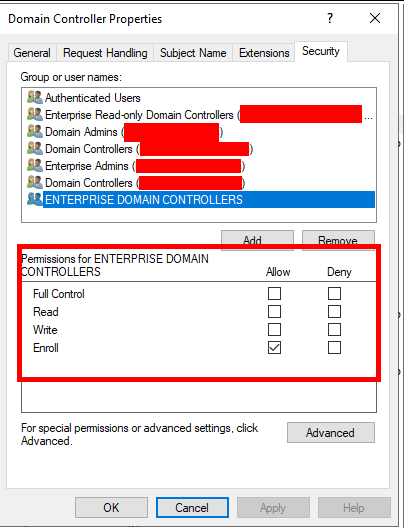
If we take a look at another Certificate Template, in this example the ‘Domain Controller Authentication’ template it does have the ‘Autoenroll’ permission available:
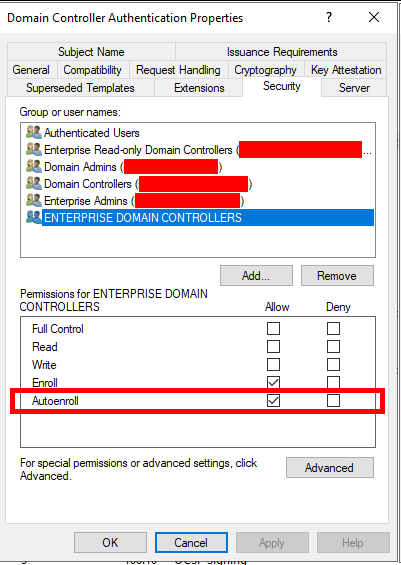
It seems a Domain Controllers default behaviour is to automatically get itself a certificate using the ‘Domain Controller’ template, if published, and will completely ignore that it does not actually have permissions to do this automatically.
If you then configure the ‘Certificate Services Client – Auto-Enrollment’ GPO, in preparation for replacing the default and deprecated ‘Domain Controller’ certificate template, the GPO will override this default behaviour in a Domain Controller causing it to respect the ‘Autoenroll’ permissions on certificate templates. Since the ‘Domain Controller’ certificate template does not have ‘Autoenroll’ permissions, Domain Controllers will no longer automatically request a certificate. I do not know if this change impacts renewals, I did not wait that long to find out.
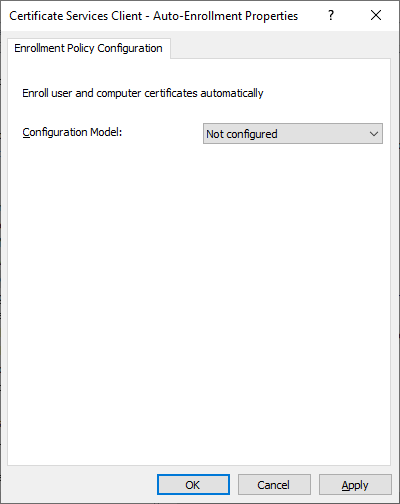
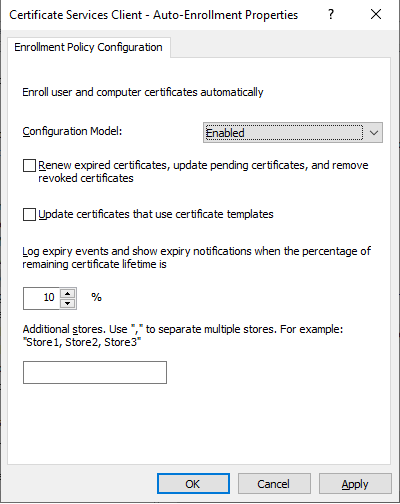
Fixing this was simple. I reverted the GPO back to ‘Not Configured’ and ran “gpupdate /force” on our Domain Controllers. After the machines group policy was refreshed the domain controller instantly requested a certificate using the ‘Domain Controller’ certificate template it technically does not have ‘Autoenroll’ permissions on.
Odds are this is going to be a rare occurrence as Microsoft’s recommendations are to use the ‘Kerberos Authentication’ certificate template for Domain Controllers these days and best practices are not to publish the default certificate templates and instead clone your own.
In my case I was prepping to move to ‘Kerberos Authentication’ templates which requires this GPO be configured for renewals to work properly. I’m just going to plan to make the GPO change right after I publish the new certificate template.