Update 2021-12-18 – This looks like a much more competent script for detecting this vulnerability and there is a python version for Linux: https://github.com/CERTCC/CVE-2021-44228_scanner
Updated 2021-12-17 – Script is v1.4 and looks for .war files now too
Original post below
Inspired by the one-liner here: https://gist.github.com/Neo23x0/e4c8b03ff8cdf1fa63b7d15db6e3860b#find-vulnerable-software-windows
gci 'C:\' -rec -force -include *.jar -ea 0 | foreach {select-string "JndiLookup.class" $_} | select -exp Path
I wrote a script to expand on the command, support Windows Server 2008 onward and to be more automated.
This script is basically the one liner with a bit of logic to get all the local fixed disks on a server and iterate through them all looking for Log4j jar file:
<#
.Synopsis
Checks the local system for Log4Shell Vulnerability [CVE-2021-44228]
.DESCRIPTION
Gets a list of all volumes on the server, loops through searching each disk for Log4j stuff
Using base search from https://gist.github.com/Neo23x0/e4c8b03ff8cdf1fa63b7d15db6e3860b#find-vulnerable-software-windows
Version History
1.0 - Initial release
1.1 - Changed ErrorAction to "Continue" instead of stopping the script
1.2 - Went back to SilentlyContinue, so much noise
1.3 - Borrowed some improvements from @cedric2bx (https://gist.github.com/Neo23x0/e4c8b03ff8cdf1fa63b7d15db6e3860b#gistcomment-3995092)
Replace attribute -Include by -Filter (prevent unauthorized access exception stopping scan)
Remove duplicate path with Get-Unique cmdlet
1.4 - Added .war support thanks to @djblazkowicz (https://gist.github.com/Neo23x0/e4c8b03ff8cdf1fa63b7d15db6e3860b#gistcomment-3998189)
.EXAMPLE
.\check_CVE-2021-44228.ps1
.NOTES
Created by Eric Schewe 2021-12-13
Modified by Cedric BARBOTIN 2021-12-14
#>
# Get Windows Version string
$windowsVersion = (Get-WmiObject -class Win32_OperatingSystem).Caption
# Server 2008 (R2)
if ($windowsVersion -like "*2008*") {
$disks = [System.IO.DriveInfo]::getdrives() | Where-Object {$_.DriveType -eq "Fixed"}
}
# Everything else
else {
$disks = Get-Volume | Where-Object {$_.DriveType -eq "Fixed"}
}
# I have no idea why I had to write it this way and why .Count didn't just work
$diskCount = $disks | Measure-Object | Select-Object Count -ExpandProperty Count
Write-Host -ForegroundColor Green "$(Get-Date -Format "yyyy-MM-dd H:mm:ss") - Starting the search of $($diskCount) disks"
foreach ($disk in $disks) {
# One liner from https://gist.github.com/Neo23x0/e4c8b03ff8cdf1fa63b7d15db6e3860b#find-vulnerable-software-windows
# gci 'C:\' -rec -force -include *.jar -ea 0 | foreach {select-string "JndiLookup.class" $_} | select -exp Path
# Server 2008 (R2)
if ($windowsVersion -like "*2008*") {
Write-Host -ForegroundColor Yellow " $(Get-Date -Format "yyyy-MM-dd H:mm:ss") - Checking $($disk.Name): - $($disk.VolumeLabel)"
Get-ChildItem "$($disk.Name)" -Recurse -Force -Include @("*.jar","*.war") -ErrorAction SilentlyContinue | ForEach-Object { Select-String "JndiLookup.class" $_ } | Select-Object -ExpandProperty Path | Get-Unique
}
# Everything else
else {
Write-Host -ForegroundColor Yellow " $(Get-Date -Format "yyyy-MM-dd H:mm:ss") - Checking $($disk.DriveLetter): - $($disk.VolumeLabel)"
Get-ChildItem "$($disk.DriveLetter):\" -Recurse -Force -Include @("*.jar","*.war") -ErrorAction SilentlyContinue | ForEach-Object { Select-String "JndiLookup.class" $_ } | Select-Object -ExpandProperty Path | Get-Unique
}
}
Write-Host -ForegroundColor Green "$(Get-Date -Format "yyyy-MM-dd H:mm:ss") - Done checking all drives"
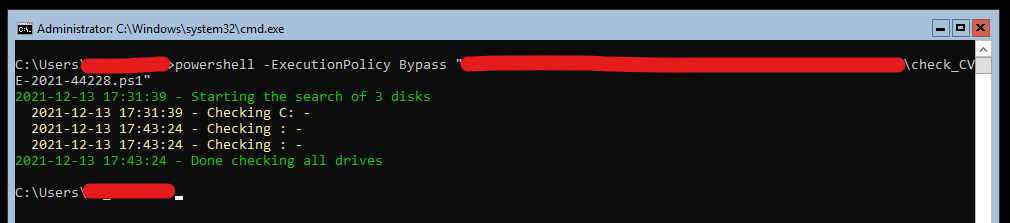
Sample output with nothing found:
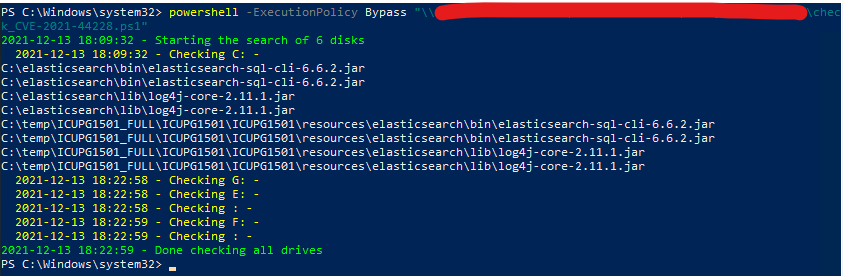
Sample output with something found:
Good luck everyone.
Great script Eric, I really appreciate you publishing this for everyone. I notice that it’s scanning drives with no letter. You can make it scan & count only fixed drives with letters by using the following command:
$volumes = Get-WmiObject win32_volume | Where { $_.drivetype -eq ‘3’ -and $_.driveletter}
Thanks! I did notice that when I was building it and decided to let it continue doing so. We don’t use mount points so any drives with no drive letter are likely un-used space or the System Recovery volume. Either way, no harm in looking I figured.
Hi,
Thank you for your work.
I try in my 2008 server. the script runs well.
i create a testlog4j.jar file into the C:\TEMP\
But is not appear during the checking of C Drive.
Regards
That is because of this: `ForEach-Object { Select-String “JndiLookup.class” $_ }`
It is looking in each found .jar file for the string “JndiLookup.class” which is associated with Log4j. If a .jar does not have that string then it should be fine.
It looks like your test file didn’t have any content in it. Try adding “JndiLookup.class” to it with Notepad and then re-run the scan.
I am posting an updated script shortly. Supposedly .war files may also be vulnerable.