CIRA (Canadian Internet Registration Authority) has recently launched a new DNS service called the “Canadian Shield” which is basically a DNS service similar to OpenDNS or Cloudflares 1.1.1.1 for Canadians, by Canadians.
CIRA offers three levels of protection depending on how safe you want to be:
- Private: DNS resolution service that keeps your DNS data private from third-parties.
- Protected: Includes Private features and adds malware and phishing blocking.
- Family: Includes Protected and Private features and blocks pornographic content.
We use the Enterprise version of this service at my place of work and based on how we use it I’d say we’re using the equivalent of their “Protected” offering. We’ve had zero issues with the service and defiantly feels like it adds an extra layer or protection to our users.
Alright, enough free advertising (I am not receiving compensation from CIRA for this post).
When this was first announced I was eager to try it at home. CIRA’s instructions are how to either configure DNS over HTTPS (DoH) on a per-browser basis (not ideal for me since I have many devices on my network and don’t only use Firefox/Chrome) or configure your outbound DNS to use their servers over traditional, un-encrypted, DNS queries.
What I really want is to configure my Pi-hole which is my DNS endpoint for anything on my network to use the new CIRA service. This would capture ALL outbound DNS traffic and send it to CIRA making it so I only have to configure things in one place.
My current setup is: Clients -> 1 of 2 Active Directory DNS Servers -> Pi-hole -> Cloudflare via DoH (1.1.1.1 / Cloudfared)
This will easily work on a more traditional deployment of: Clients -> Pi-hole -> Cloudflare via DoH (1.1.1.1 / Cloudfared)
My Pi-hole is a basic CentOS 8 VM with the Pi-hole software installed on it with cloudflared so I can take advantage of DoH for all of my outbound DNS traffic. This is the minimum you need to get this working, a functional Pi-hole that is already sending it’s outbound DNS queries to Cloudflare (or another DoH provider) via cloudflared.
The first thing I did was re-configure my cloudflared to simply try using the CIRA DoH:
# Edit the cloudflared configuration file vim /etc/default/cloudflared # Commandline args for cloudflared to use 1.1.1.1 CLOUDFLARED_OPTS=--port 5053 --upstream https://1.1.1.1/dns-query --upstream https://1.0.0.1/dns-query # Changed the above to: CLOUDFLARED_OPTS=--port 5053 --upstream https://private.canadianshield.cira.ca/dns-query # Save and close the file # Restart cloudflared systemctl restart cloudflared # Test DNS nslookup google.ca # This failed
This ended up not working and after I tried it I realized why. To be able to use private.canadianshield.cira.ca you have to have functioning DNS. Cloudflare has skirted this issue by using 1.1.1.1 and 1.0.0.1 for it’s service, they are IPs and do not need DNS to be working to function.
Fortunately the solution was very easy:
# I did a nslookup on the specific CIRA service I wanted to use (Private) via traditional DNS nslookup private.canadianshield.cira.ca 1.1.1.1 Server: 192.168.0.4 Address: 192.168.0.4#53 Non-authoritative answer: Name: private.canadianshield.cira.ca Address: 149.112.121.10 Name: private.canadianshield.cira.ca Address: 149.112.122.10 Name: private.canadianshield.cira.ca Address: 2620:10a:80bb::10 Name: private.canadianshield.cira.ca Address: 2620:10a:80bc::10 # If you want to use Protected or Family instead of private # do a nslookup on either protected.canadianshield.cira.ca # or family.canadianshield.cira.ca instead and use those IPs # I then edited my /etc/hosts file on my Pi-hole vim /etc/hosts # and added the following (I don't use IPv6 at this time): # CloudA DNS 149.112.121.10 private.canadianshield.cira.ca 149.112.122.10 private.canadianshield.cira.ca # Save and close the file # Test DNS nslookup cira.ca Server: 192.168.0.4 Address: 192.168.0.4#53 Non-authoritative answer: Name: cira.ca Address: 52.60.203.65
That’s it. I now have the CIRA Canadian Shield working on my Pi-hole using the cloudflared software.
Now for some DNS benchmarks, what’s faster? CIRA or 1.1.1.1?
I flushed the DNS cache on my Active Directory DNS servers and then restarted cloudflared on my Pi-hole before running these benchmarks:
1.1.1.1.1 / 1.0.0.1
192.168. 0. 4 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.009 | 0.052 | 0.196 | 0.043 | 100.0 |
+ DotCom Lookup | 0.009 | 0.013 | 0.027 | 0.004 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
CAYENNE.nom.fizi.ca
Local Network Nameserver
192.168. 0. 5 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.009 | 0.051 | 0.195 | 0.044 | 100.0 |
+ DotCom Lookup | 0.010 | 0.014 | 0.028 | 0.003 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
HORSERADISH.nom.fizi.ca
Local Network Nameserver
and here are the three CIRA services:
CIRA - Private
192.168. 0. 4 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.019 | 0.062 | 0.236 | 0.048 | 100.0 |
+ DotCom Lookup | 0.022 | 0.046 | 0.086 | 0.020 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
CAYENNE.nom.fizi.ca
Local Network Nameserver
192.168. 0. 5 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.014 | 0.068 | 0.238 | 0.056 | 100.0 |
+ DotCom Lookup | 0.023 | 0.047 | 0.075 | 0.019 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
HORSERADISH.nom.fizi.ca
Local Network Nameserver
CIRA - Protected
192.168. 0. 4 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.019 | 0.062 | 0.236 | 0.048 | 100.0 |
+ DotCom Lookup | 0.022 | 0.046 | 0.086 | 0.020 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
CAYENNE.nom.fizi.ca
Local Network Nameserver
192.168. 0. 5 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.014 | 0.068 | 0.238 | 0.056 | 100.0 |
+ DotCom Lookup | 0.023 | 0.047 | 0.075 | 0.019 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
HORSERADISH.nom.fizi.ca
Local Network Nameserver
CIRA - Family
192.168. 0. 4 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.014 | 0.064 | 0.246 | 0.053 | 100.0 |
+ DotCom Lookup | 0.022 | 0.039 | 0.080 | 0.018 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
CAYENNE.nom.fizi.ca
Local Network Nameserver
192.168. 0. 5 | Min | Avg | Max |Std.Dev|Reliab%|
----------------+-------+-------+-------+-------+-------+
+ Cached Name | 0.000 | 0.000 | 0.000 | 0.000 | 100.0 |
+ Uncached Name | 0.014 | 0.073 | 0.248 | 0.062 | 100.0 |
+ DotCom Lookup | 0.024 | 0.049 | 0.082 | 0.020 | 100.0 |
---<-------->---+-------+-------+-------+-------+-------+
HORSERADISH.nom.fizi.ca
Local Network Nameserver
If I am interpreting this data correctly, CIRA is 0.010s-0.030s slower on average compared to 1.1.1.1. Hardly worth mentioning.
I’m happily switching over to a Canadian based DoH service (full disclosure, I’m Canadian). No offence Cloudflare, you still get to hold my DNS until CIRA starts offering their DNS Anycast Service for home users (hint hint).
Oh and just in case your curious, if you choose their ‘Family’ service and try and hit up Pornhub, you’re greeted with this:
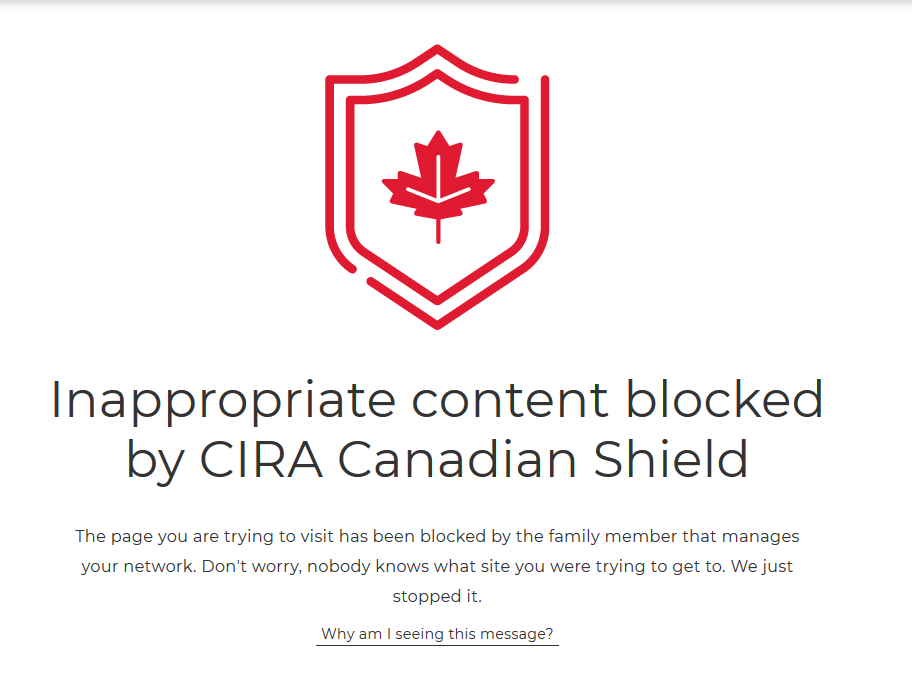
Hi,
According to you according to the same reasoning, will their suggested configuration for Chrome, without modifying the Windows DNS or router, also fail without modifying the Windows DNS?
And if so, how can we be sure that we are under DNS over HTTPS with Chrome with their configuration? Everyone has been tested for Cloudflare, but only seems to work for Cloudflare DNS.
Thank you
Just did a quick test and if you configure Chrome/Firefox using their suggested settings Chrome/Firefox will use your operating systems DNS configuration to lookup (private|protected|family).canadianshield.cira.ca first and then Chrome/Firefox will use DoH and CIRA to lookup whatever your trying to browse. So as long as your operating systems DNS is working properly so will their Chrome/Firefox configuration.
If your operating systems DNS (or your router if your operating system uses your router for DNS) is not using DoH then your ISP will be able to see that you looked up (private|protected|family).canadianshield.cira.ca but not what you looked up. Better than nothing.
The best way to determine if your using DoH for DNS lookups would be to run a packet capture on your computer using Wireshark. With the packet capture going, disable DoH in Chrome/Firefox and go to a website of your choosing. Then enable DoH in Chrome/Firefox and go to a different website. Stop your package capture and filter on ‘dns’. You should in theory only see a DNS lookup for the first website and not the second website and in place of the second website you should see a DNS lookup for (private|protected|family).canadianshield.cira.ca.
I tried to test this but I’ve put some other mitigation in place on my network to make sure Firefox doesn’t use DoH at all.
Thank you, much appreciated. I will try this!
Hello again,
I had fun with this software by trying several configurations. I am far from being a pro, but finally, here are my results.
On Chrome (after enabling DNS over HTTPS):
– 8.8.8.8 and 1.1.1.1, works fine, DNS captures stop
– With CIRA, whatever the configuration, nothing works, I don’t know why, I can put the address of CIRA in the Chrome shortcut as shown and add the DNS addresses of CIRA in Windows, activate, disable or leave the default option of DNS over HTTPS in Chrome, the DNS continues to register for each site visited.
On FireFox:
– I just tested with CIRA the DNS over HTTPS option. It works, although with each search, a DNS record does this, but without anyone knowing for where.
So there you are, I may be missing something in the configuration of Chrome with CIRA, but I can’t do it, when I can do it easily with the others.
I say that, and it may not really be the case, but since Chrome now allows you to activate the DNS over HTTPS function, is it possible that the configuration which consists in putting the address in Chrome shortcut target no longer works?
Thank you
Thanks for sharing the info.
Thanks for this. I’ve been using Canadian Shield at home for nearly a year. Last summer, I started experimenting with Pi-hole. In my research I stumbled on the DoH subject and a configuration for cloudflared to use 1.1.1.1. I liked the idea, but I still wanted to benefits of CIRA. So I started searching, and here I am.
I was under the impression however that CIRA only offer their DoH service to paying customers whereas the free service does not provide DoH support. I can’t remember where I read this. Am I mistaken? If I am, then I’m delighted to know that I can continue using Canadian Shield and now be able to use my Pi-hole configuration for DoH.
As far as I can tell it’s all completely free. I’ve been using DNS over HTTPS from them since they launched.
If you go to https://www.cira.ca/cybersecurity-services/canadian-shield and click ‘DNS Encryption’ near the bottom the info is right there for anyone to use.
Ah yes, I see it now. Thank you for pointing that out. I even see it in their comparison chart of their Canadian Shield service vs the DNS Firewall subscription service (both have DoH in common).
On that note, have you considered simply using the CIRA IP addresses for the upstream in the cloudflared config file rather than adding them to the hosts file?
Thanks again.
I’m fairly certain when I initially tried this using the https:/// resulted in a SSL error and cloudflared wouldn’t work.
Editing the hosts file gets around this problem. It’s a bit of a chicken and the egg kind of thing.
With out working DNS you can’t use DoH to lookup the CIRA DNS servers. Cloudflare gets away with this because they are using IPs and got SSL certificates for those IPs which I don’t think you can normally do.